Secure communication has become a vital requirement on the Internet. Lots of information transferred through the Internet are sensitive data such as financial transactions, medical information, media streaming etc. To ensure security of data transferred on the Internet, a few secure protocols have been designed including SSL/TLS and IPsec. Many large websites in the world have adopted TLS. Apart from SSL/TLS, there is some other protocol designed to be used in special cases. One of them is the DTLS -- Datagram Transport Layer Security protocol.
What is DTLS
DTLS is a secure data transfer protocol used to encrypt data transferred over datagram protocols(typycally UDP). The DTLS protocol provides communications privacy for datagram protocols. It is based on the Transport Layer Security (TLS) protocol and provides equivalent security guarantees. DTLS is defined in RFC 4347 and RFC 6347.
Why DTLS
SSL/TLS is designed to be working over reliable transport channel(typically TCP). SSL/TLS cannot tolerate data loss and out of sequence data records. If a data record is coming in out of sequence, the data record may not be decrypted correctly but with MAC verification error. What if an application is built based on UDP? The data record may be out of sequence or may be lost, what if the data security of this kind also needs to be guaranteed? This is why DTLS is designed.
How it works
DTLS isl based on TLS but with some changes to adapt to the UDP communications. These major changes include :
- Add explicit sequence number field to record. This ensures data can be reordered correctly when it's out of sequence. In TLS, the sequence number is in the encrypted record MAC and can be verified only after the decryption. In DTLS, this is not possible since data may get lost
- Drop support of some cipher suites used in TLS. Stream ciphers are banned in DTLS since the decryption of data in stream cipher depends on the previous decrypted data. These ciphers cannot be used in DTLS as data may get lost. Typically, RC4 cannot be used in DTLS.
- Add retransmission mechanism in case of packet loss. There is a retransmission timer which will retransmit a packet after some timeout if it sending side doesn't get the correct response.
- Change the alert mechanism for MAC verification failure. In TLS, if a MAC verification fails, then a fatal error will be sent and the connection will be invalidated. In DTLS, if a MAC verification fails, the recommended method is just drop the record received without aborting the connection.
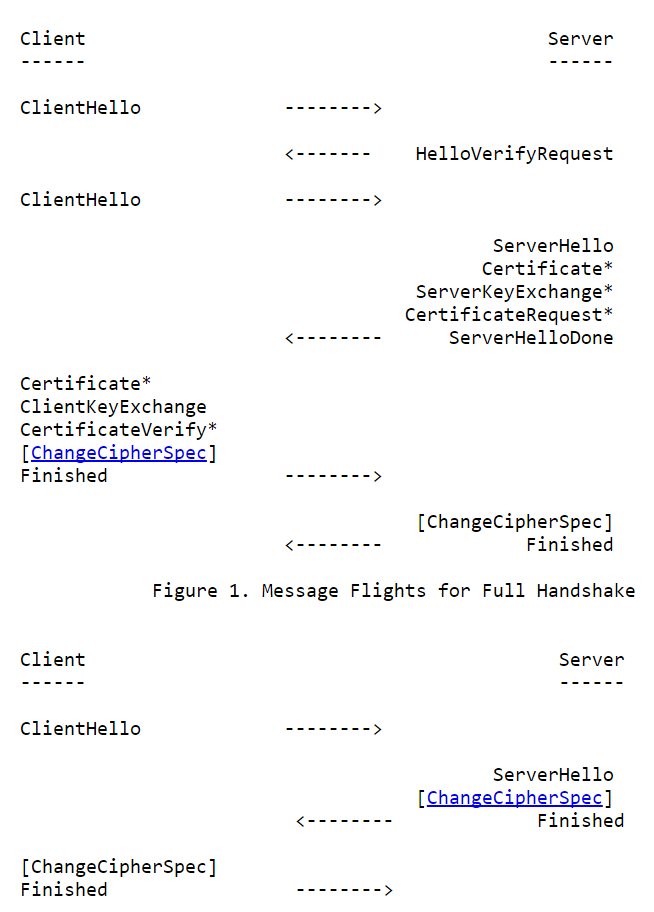
- A new record message is added -- HelloVerifyRequest. HelloVerifyRequest is designed to prevent DoS attacks. Since data security protocols are vulnerable to DoS attacks, to prevent these attacks. HelloVerifyRequest will be used to identify the sender of the ClientHello is not faked with invalid IPs. The HelloVerifyRequest is designed to be small and it contains a cookie which is used to identify the client. After the client sends the ClientHello message, server SHOULD reply with a HelloVerifyRequest and then the client will send the ClientHello again with the cookie from HelloVerifyRequest attached. Then the rest of handshake will continue.
Where to use
DTLS can be used in many applications designed based on datagram protocols. These applications include IM application, gaming application etc.
Now there are quite a few libraries have support of both DTLS v1 and DTLS v1.2. Some of them are OpenSSL, NSS. Java 9 is also planning to add support of DTLS.